Monitor and Respond to Security Threats with Azure Sentinel
Start use Azure Sentinel for your organization.
Introduction
Nowadays we are facing a world full of online danger which we want to detect and purge! With that comes allot of data and time to process all the data to see where certain threats are hiding. To make it humans easier to hunt for threats that reside in their environment we tend to create systems to provide assistance in the processing of the data. This way we can spend more time in thinking about the route we want to take to detect a certain situation. With that said, Azure Sentinel is such system. It is built by Microsoft and is currently in thé top leaders for cloud-native Security Information and Event Management (SIEM) solutions. It has been developed as a powerful tool for detecting and hunting cyber threats.
Below an example how the Azure Sentinel Overview page looks like. 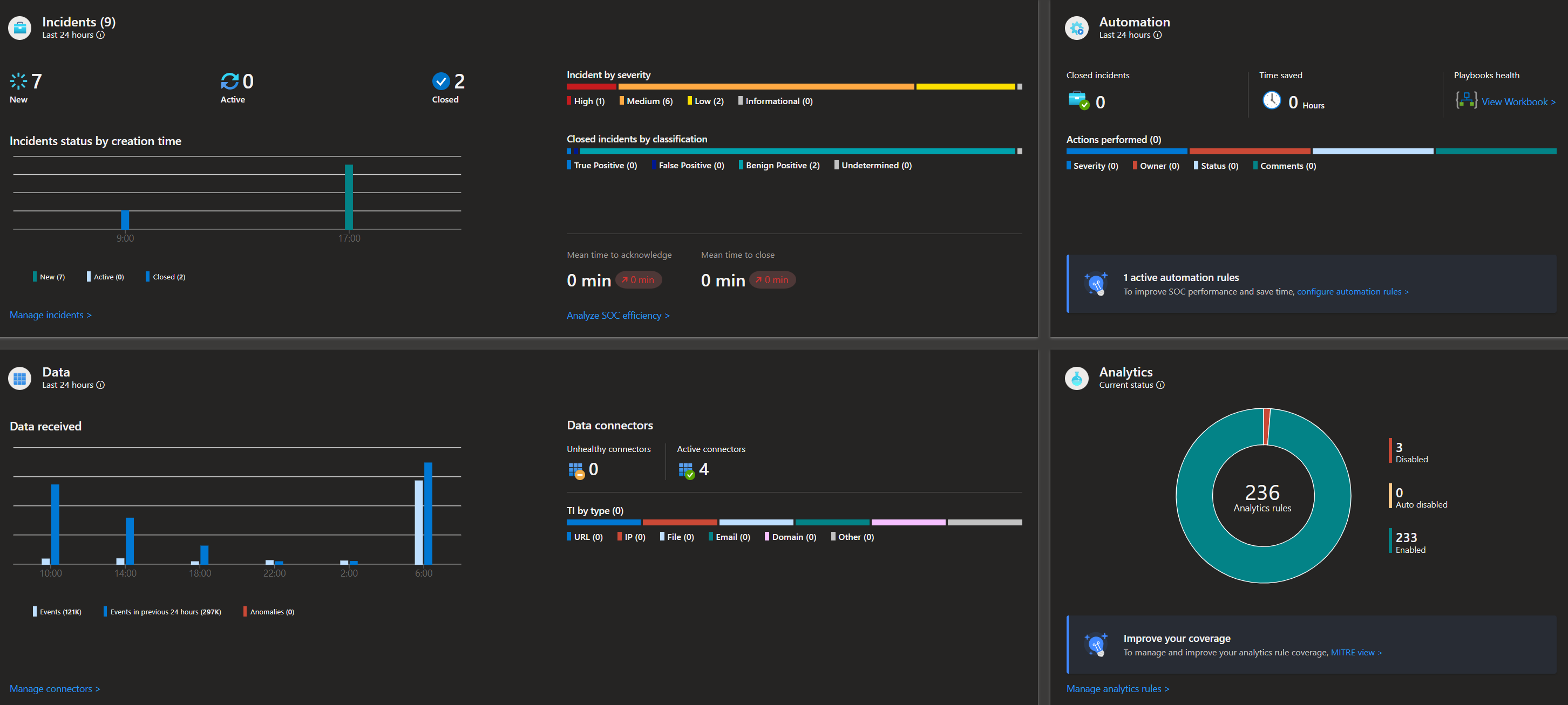
Proactive Threat Detection with Azure Sentinel
With the use of advanced analytics and machine learning capalities, Azure Sentinel is able to detect in a proactive way. By collecting, processing and analyzing lots of data it can detect threats quicker than a SOC analyst can do by its own. Therefore it is a great tool for SOC analysts to identify threats in an environment. The system will use defined rules with a query behind it which will search for the given pattern. Once a threat has been identified by the pattern that the analytic rule is setup with, it can generate an alert/incident to be shown in the Azure Sentinel Dashboard for the SOC analyst to investigate.
This makes the use of Azure Sentinel a proactive threat detection tool.
Automate Incident Response with Playbooks
Azure Sentinel is able to make use of Azure Logic Apps which allows organizations to create automated playbooks for most common incident scenarios. These playbooks can be triggered by specific alerts or events happening, and can run the logic app to run actions such as sending notifications, creating a team in Teams, or remediate common incidents by a certain action which fits the incident. By using these automations the SOC analysts can spend more time investigating more complex incidents that require focus.
Enriching Alerts
One of the challenges that SOC analysts faces is the understanding of the context of an alert they are investigating. The question rises, why is the alert generated based on the data in the query of the alerttemplate? What is the relevance and the severity of an alert? To help the SOC analyst getting answers to these questions we can enrich these alerts by adding tags such as the used technique and tactic. Another addition is entities. By using entities you can identify which devices, users or resources were involved in the incident.
The power of community!
Yes! Azure Sentinel has a whole community who loves to build and improve detection rules and make the product even better as it already is. Azure Sentinel’s integration with Microsoft’s threat intelligence feed and community-driven resources like the Azure Sentinel GitHub repository enables organizations to access up-to-date threat intelligence and best practices. These resources can be used to enhance detection rules, create custom analytics queries, and improve overall security posture.
Conclusion
Enhanced Visibility:
Azure Sentinel offers a unified view of your entire security landscape, making it easier to monitor and manage security incidents across your organization.
Rapid Threat Detection:
Azure Sentinel can quickly detect and identify potential security threats in your environment, helping prevent data breaches and unauthorized access.
Automated Incident Response:
Azure Sentinel can automate routine tasks and coordinate responses to detected threats. This will allow security teams to focus on more critical issues.
Customizable Alerts:
With Azure Sentinel, you can create your own custom alerts and rules. This way you can fit it for your organization needs and that of your customers to ensuring you’re notified of the most relevant threats and incidents.
Azure Sentinel has proven to be an invaluable tool for organizations seeking to bolster their defences. Although building up Azure Sentinel to full capacity can be a complex and time consuming project in your organisation/customers tenant, keep making steps. Bit by bit you will learn, create, think, re-create and finally get more insights by every step you take.
